Credit rating card fraud — the theft and unauthorized use within your credit history card facts — can wreak havoc on your own finances and credit scores. Fortunately, you can help safeguard your credit card from intruders by recognizing the indications of fraud and getting methods to secure your own information.
All through the report, We have now emphasized the value of cybersecurity and the need to prioritize the protection of private economical information and facts.
On the subject of securing your online routines, particularly from the realm of PHP proxy and SSL connections, ForestVPN provides sturdy encryption and privateness features. Through the use of ForestVPN, you can be certain that your PHP proxy connections are encrypted, introducing an extra layer of stability versus prospective threats like eavesdropping or info interception.
Regardless of whether their cards have EVM, individuals usually tend to utilize the magnetic stripe at POS terminals a result of the familiarity making it possible for their credit history card information to probably be stolen.
There are two main techniques in credit score card cloning: getting credit history card information and facts, then developing a fake card that may be useful for purchases.
So So how exactly does card cloning operate in the complex feeling? Payment cards can retail outlet and transmit information and facts in various various ways, Hence the applications and techniques accustomed to clone cards could vary depending on the condition. We’ll explain below.
Our System provides a trusted and discreet Resolution for experts in fraud detection, process testing, and schooling.
Usually, the skimmer is placed excessive of the first card reader but is so related in dimensions, shade, and texture that it’s challenging to detect. The skimmer could also be put in Within the terminal, or alongside exposed wiring.
Whilst phishing requires the cardholder truly sharing their data Along with the scammer, a similar can not be claimed about cloning or skimming.
But precisely what is card cloning just, And the way do thieves copyright information and facts? We are going to examine this and much more in nowadays’s in depth information on card cloning.
That's why it really is very important for people to concentrate on the approaches used in credit card cloning and get necessary precautions to guard on their own from falling victim to this kind of fraud.
Skimming frequently comes about at gas pumps or ATMs. But it can also occur if you hand your card more than for payment, particularly if it leaves your sight. For illustration, a shady waiter skims your credit card info that has a handheld gadget.
Verify your accounts and credit card statements usually, if not once per day. It is significant to observe account website action soon after producing a order or transaction at a place you haven't performed so ahead of. Should your statements change drastically, You could have been tricked by skimmers.
Consider updating your passwords together with other security measures for any accounts connected with your card.
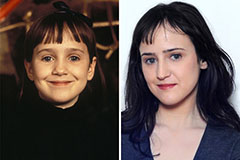 Mara Wilson Then & Now!
Mara Wilson Then & Now! Devin Ratray Then & Now!
Devin Ratray Then & Now!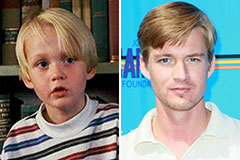 Mason Gamble Then & Now!
Mason Gamble Then & Now! Danica McKellar Then & Now!
Danica McKellar Then & Now! Meadow Walker Then & Now!
Meadow Walker Then & Now!